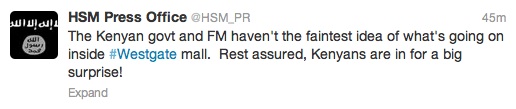
A document found after Somali troops killed Fazul Abdullah Mohammed, al Qaeda’s former leader in East Africa and a senior Shabaab commander, details a plot to conduct multiple Mumbai-like attacks that target civilians in London. The plot highlights how al Qaeda and Shabaab seek to strike civilian targets outside Somalia, and foreshadowed Shabaab’s attack on the Eastgate Mall in Kenya this week.
The document and several others found in Fazul’s possession after he was killed by Somali troops at a checkpoint in Mogadishu in June 2011 were obtained by the Toronto Star. A copy of the document was also obtained by The Long War Journal. The Canadian newspaper reported that “dozens of documents, Internet frame grabs and media reports in English, Arabic, Somali and Swahili, along with more than 50 video clips” were also found in Fazul’s car.